Hi ,
This is going to be my first technical article on my blog.For everyone's benefit, I would like to start from basics.lets see how to set up telnet and SSH access to a switch / Router. SSH and telnet very diffrent from security prespective.Telnet is unsecured management protocol whereas SSH is a secure management protocol.SSH uses RSA signature to encrypt the traffic.
Telnet :
Its simple to set up
Changing default port number in telnet :
Changing default port number of telnet is good idea to restrict unauthorized access.
This is going to be my first technical article on my blog.For everyone's benefit, I would like to start from basics.lets see how to set up telnet and SSH access to a switch / Router. SSH and telnet very diffrent from security prespective.Telnet is unsecured management protocol whereas SSH is a secure management protocol.SSH uses RSA signature to encrypt the traffic.
Telnet :
Its simple to set up
How to create a telnet user name and Password
login to global config mode use follwing commands. Here username is given as 'cisco' and password is 'cisco123'. 'login local' command is used to point the switch to local database during authentication of a user.
While seting up a telnet session make sure that only appropriate user should be only able to access the devices. To restrict all other users from accessing telnet we need create a access list permitting only one ip. After that we need apply an access class in corresponding line vty.
Changing default port number in telnet :
Changing default port number of telnet is good idea to restrict unauthorized access.
Telnet is
a tcp connection. By default it uses port 23. We can change this port using
rotary command.
Note that
rotary has a base number 3000, so if you give rotary 25 it will be considered
as 3025.
In next
step we need to block default telnet port from using via access list and allow
remaining traffic.
Now
go to line vty and apply acl as access class
Thats it. Now we can access telnet using port 3025 via telnet. Default port 23 will be blocked. My gentle advice is that never use telnet for a connection simply because it is not secure. Telnet will send management traffic in clear text which helps the hackers to read them.
SSH
SSH is the most secure way to manage devices.SSH uses RSA signature to encrypt the communication between the manager and end device.Steps invloved in setting up SSH are.
Step 1 :
Create a local user name and password
Step
2 : Create a domain name
Step 3: Create RSA keys
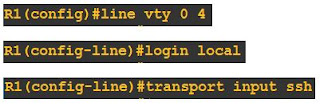
Step 4 :
Apply in line vty
When
we give command transport input ssh all telnet connections will refused by
default.